Key Takeaways:
- Security awareness training builds human resilience, not just compliance. Teach employees to spot manipulation, urgency, authority, and traps before they click.
- Phishing and social engineering dominate breaches. Train teams to pause, verify, and report suspicious messages to strengthen your human firewall.
- Strong passwords and MFA protect accounts. Use password managers and app‑based multi-factor authentication (MFA) with number matching. Avoid SMS fallbacks to stop credential attacks.
- Backups and ransomware readiness ensure data recovery. Combine awareness training with immutable backups and fast restore through Veeam Data Platform.
When employees understand how attackers think, they become your first line of defense, not your weakest link. Yet, for many organizations, security awareness training has turned into a compliance checkbox rather than a meaningful exercise in risk reduction.
The goal of awareness training is to build a resilient workforce that can recognize and resist today’s most common attack vectors like phishing, credential theft, and, most importantly, social engineering. When combined with strong data protection and reliable backups through platforms like Veeam Data Platform, organizations can transform their human layer into an active part of their cyber-resilience strategy.
Why Security Awareness Training Matters
Cybersecurity today is as much about people as it is about technology. Attackers know that manipulating the human psyche is often faster and easier than exploiting software vulnerabilities. That’s why, globally, over 80% of breaches still involve some form of human error or social engineering (according to the Verizon DBIR 2025).
Beyond Compliance: The Psychology of Persuasion
Let’s consider an example like the MGM ransomware attack of 2023, where the Scattered Spider group bypassed technical controls by impersonating IT staff over the phone. The key to the group’s success was influence.
From Awareness to Resilience
Training alone can’t prevent every click, but it can dramatically reduce risk when paired with strong operational resilience. Teaching employees to report suspicious activity promptly without fear of repercussion and showing them the anatomy of social engineering attacks builds human resilience. At the other end of the resiliency spectrum, ensuring your data is backed up, isolated, immutable, and recoverable through tools like Veeam Backup and Recovery closes the loop between human vigilance and technical protection.
Why Password Complexity isn’t the Whole Answer
For years, organizations have forced long, complex password rules and frequent rotations. The result? People wrote them down, reused them across accounts, or stored them in unsecured notes apps. Complexity without convenience simply pushes users toward unsafe workarounds. See this new NIST guidance.
Another important point is that organizations should look for enterprise password managers that identify when emails may have been in a breach. HaveIBeenPwned offers integration with many password managers or even enterprise solutions.
| Pause before you click | If an email or link feels slightly off, it probably is. |
| Check the URL | Look for “https://” and verify the domain name. Attackers often use subtle misspellings or extra characters. Even this can be tricky due to typosquatting, which can use different characters (homoglyphs) to fool the eye. |
| Avoid free or unverified downloads | Software from unofficial sources is one of the easiest infection vectors. |
| Use work email for work only | Mixing personal and professional accounts increases exposure. |
| Double‑check recipients | Before sending sensitive information, confirm the “To” field. It’s easy to send confidential data to the wrong contact. |
| Respect your anti‑malware alerts | If your endpoint protection flags a file or website, don’t override it. Report it. |
These rules might sound simple, but when these are implemented well with technology, process, and importantly user education, it can be very effective against attacks.
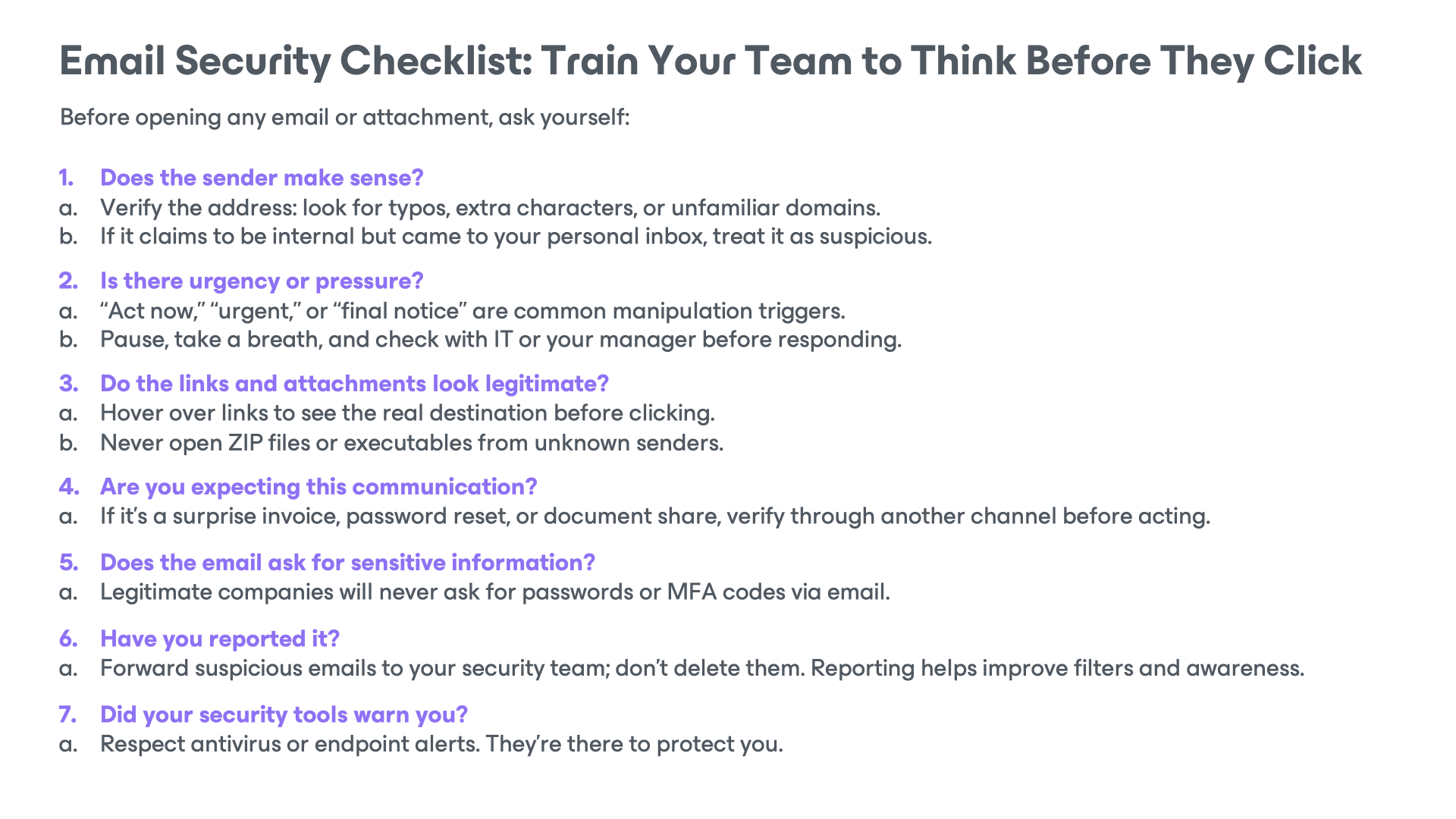
Data Protection, Backups, and Ransomware Readiness
Even with the best training, someone will eventually click the wrong link or approve the wrong request. That’s just a reality. What matters next is how quickly the organization can detect, contain, and recover .
Understanding Ransomware’s Growing Impact
Ransomware remains one of the fastest‑growing cyberthreats, now factoring into 44% of all breaches worldwide . Attackers encrypt data and demand payment, but the real damage comes from downtime, lost productivity, and reputational harm.
Awareness training plays a critical role here. Employees need to recognize ransomware signs early, such as files failing to open, systems slowing down, or ransom notes appearing, and know how to respond.
Training for Prevention and Response
A complete awareness program should cover both:
| Prevention | Treat urgent or unexpected messages as suspicious.
Don’t download or enable macros in email attachments. Report anomalies immediately to security operations. |
| Response | Disconnect the device from the network if infection is suspected. AlertIT or the Security Operations Center (SOC) right away. Avoid rebooting or deleting files and preserve evidence for analysis. |
Fostering a Security‑First Culture
Technology can stop malware, but only culture can stop complacency. In every organization I’ve worked with, the biggest difference between average security and great security comes down to how people think, not what tools they use.
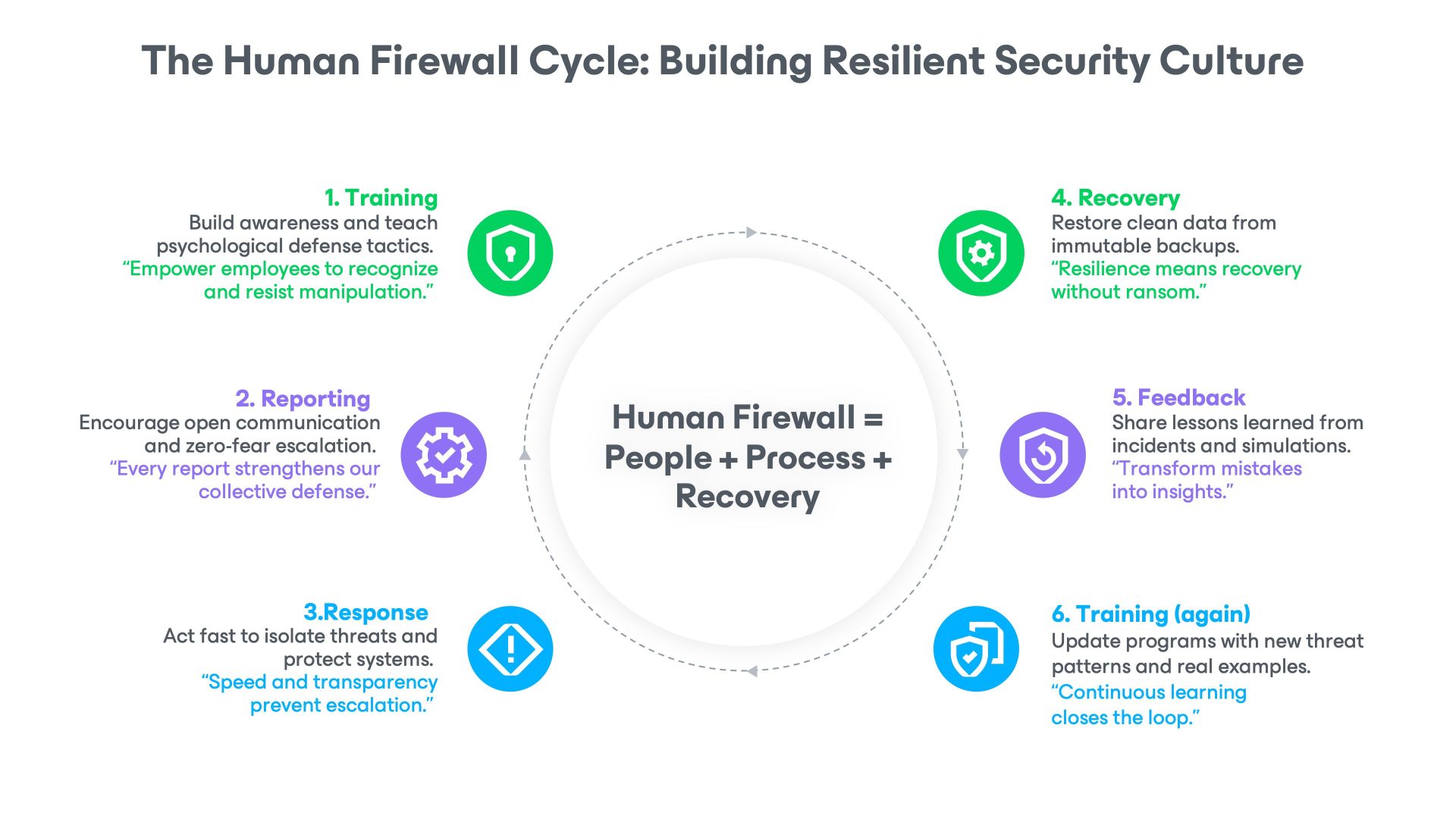
Beyond Fear and Punishment
Too often, awareness programs rely on fear: Fail a phishing simulation three times, and you’re reprimanded. Instead of security, that approach this builds silence. Employees stop reporting mistakes because they’re afraid of consequences.
A genuine security‑first culture treats errors as opportunities to learn. When someone clicks a phishing link, the question shouldn’t be “Who do we blame?”
It should be “Why did this message look convincing?”
Continuous Learning, not Checkbox Training
Security awareness shouldn’t be treated as a compliance exercise. It’s a living program that evolves with the threat landscape. That means:
- Updating training materials quarterly to reflect new attack trends.
- Sharing real examples of phishing attempts or social engineering tactics seen in your own business.
- Encouraging employees to bring in examples they’ve spotted, from suspicious emails to fake calls.
Make it fun and engaging. I’ve seen successful training in some organizations where they offer prizes for hackathons (technical) or for non-technical, prizes for reporting phishing. Embed awareness into other parts of training (new hire onboarding, for example) or even company all-hands where security teams should share demos or success stories. When people participate, they take ownership. And ownership is the foundation of a security‑first culture.
Linking Human Awareness to Resilient Systems
An organization’s security culture should foster an environment where employees can feel confident about reporting a mistake or something that doesn’t look right. This is why highlighting success stories and fostering a culture of positivity will reduce the risk of employees either not bothering to report or hiding mistakes. Pair training with a strong technical backbone that includes immutable backups, tested recovery plans, and transparent communication.
Together, human vigilance and reliable infrastructure form a complete defense. As I often tell teams, awareness protects the entry points; resilience protects everything else.
Ready to Strengthen your Organization’s Human Firewall?
Explore how Veeam Data Backup and Recovery supports a resilient, security‑first culture, and free trial to see how fast secure recovery can be.
FAQs:
How often should we conduct security awareness training for employees?
At minimum, hold formal training annually and reinforce it quarterly with short refreshers or phishing simulations. Threats evolve quickly, so frequent and lighter touchpoints keep employees alert without overwhelming them. Awareness is continuous, not a once‑a‑year exercise.
My company is small; do we really need all this security training?
Yes. Small and mid‑size businesses are prime targets because attackers know defenses are often less formalized. Even basic training on phishing, passwords, and backups can prevent costly breaches. A small company with cyber‑aware staff is harder to exploit than a large company with complacent users.
How can we make security awareness training engaging for employees?
To make security awareness training engaging, focus on interactive and practical experiences. Replace long lectures with short videos, quizzes, and real-world examples that employees can relate to. Add phishing simulations, live Q&A sessions, and small rewards to boost participation. Most importantly, include live training, in-person or remote. A live, interactive format gives employees the chance to ask anything (yes, even the “stupid” questions). When training feels relevant and hands-on, employees learn faster and retain more
What topics should every security awareness program include?
Cover phishing and social engineering, password security and MFA, device and remote‑work safety, safe internet and email practices, and ransomware readiness. Together, these build a complete human firewall and align awareness with data protection and recovery strategies.
How does security awareness training support data resilience?
We know that most breaches occur due to social engineering. The fact that AI jailbreaking is a “thing” is case and point. Humans can be far more effective at detecting social engineering taking place than machines. Your employees can be a force multiplier in ransomware defenses when combined with data resilience.
The post Top Security Awareness Training Topics Every Company Should Cover appeared first on Veeam Software Official Blog.
from Veeam Software Official Blog https://ift.tt/82WXQiY
Share this content:
